In the first part of the Bitcoin whitepaper, we have looked at the topics overview, introduction, and transactions. In the following 2nd part we will look at the topics timestamp server, proof-of-work, networks, and incentives. The chapter numbers are based on those of the whitepaper.
Table of Contents
Toggle3. Timestamp server
Annotation: Before diving into the whitepaper chapter, Satoshi had implemented as a timestamp in the first Genesis Block created the headline of the London Times ” Chancellor on brink of second bailout for banks”. This had a symbolic character in addition to its function as a reference. But now to the chapter content
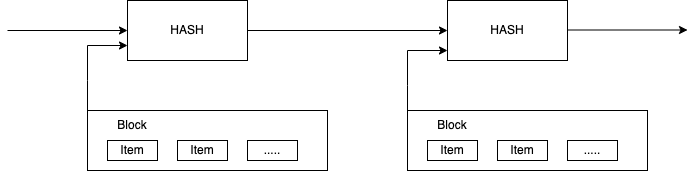
the timestamp server takes the hash of a block and posts it widely in a newspaper or Usenet post. The block contains records that are time-stamped. This proves that the data existed at that time. Otherwise, there would be no hash of them. Each timestamp also contains the preceding timestamp in its hash and forms a chain. This reinforces the previous timestamp in each case.
Annotation: This mentioned chain already suggests the famous word blockchain. The information in an individual block are the timestamps for each transaction.Timestamps prevent the so-called double-spending. With double-spending, a user would perform two similar transactions simultaneously with the use of only one token. The timestamp prevents the falsification of files
4. Proof-of-Work
The proof of work solves the problem of determining the representatives in the case of majority decisions. A CPU basically has one vote and the majority decision is represented by the longest chain. This is the chain in which the most effort was invested. An attacker would have to recreate the block itself and all blocks after it to change a past block in order to catch up and overtake the honest nodes. The possibility of an attacker catching up decreases exponentially as more subsequent blocks are added.
The difficulty level, which is determined by a moving average, can be used to compensate for the increasing hardware performance and the time-varying interest to run a node.
The moving average targets an average number of blocks per hour. If the blocks are generated too fast, the difficulty increases.
5. Network
- All nodes receive all transaction
- All new transactions are collected in a block per node.
- Each block tries to find a difficult proof of work for its block
- Once the proof of work is found, it transmits the block to all nodes
- A block is only accepted by the nodes if the transactions it contains are valid and have not already been made.
- The block is accepted by the other nodes by creating the next block in the chain which uses the hash of the accepted block as the preceding hash.
By assuming that the longest chain is the correct one, the nodes work to further extend it. If two nodes receive different versions first at the same time, they continue to work on the version received first. However, they save the other branch in case it becomes longer. As soon as one of the two branches becomes longer, all nodes will switch to the longer branch and continue working there.
New transactions do not always have to reach every node. As long as they reach many nodes they will be included in a block. The network is also fault-tolerant against lost messages. Nodes recognize when they are missing a block and request it.
Annotation: The Bitcoin network is the first global system for consensus building and beyond far beyond the payment function. It is a freely programmable economic and financial system that can be further developed by anyone. Through the peer-to-peer design, each participant of the network is directly connected to other equal participants.
My generation can still remember Napster the so-called file sharing system which made the sharing of audio, movies, and other files possible. This was a centralized P2P system that required a central server to manage the data. With Napster, the peer-to-peer architecture became popular in 1999. However, there are different forms and the algorithm of Napster is still controversial for the designation of true P2P. Other well-known P2P networks include BitTorrent, Tor, and Bitcoin. However, there are countless more and P2P is a universe in itself.
6. Incentives
The Genesis Block Satoshis started the creation of new coins. New coins are created by the node operators through the validation of transactions. Just as gold was mined in the past, node operators are now mining new coins with their transaction validations. That is why they are also called miners. The mining of coins serves as an incentive to the miners to provide their CPU power and electricity.
In addition, the transaction fees can lead to further incentives. This means that the miner receives incentives from both the mining and the transaction fees. Later, once a predetermined number of coins are in circulation, the incentives can be completely covered by the transaction fees and thus be completely inflation-free.
These incentives also serve the aspect of motivating honesty. If an attacker were able to spend more CPU power than all honest miners, he would have the opportunity to steal back his transactions or mine new coins. By making the incentive to cheat more profitable, such behavior is prevented. The technological challenge of generating so much power to launch an attack will not be discussed here.
Annotation: For a closer look at the interplay between mining and transaction fees, the following articles may be helpful.
The original whitepaper about Bitcoin can be downloaded in different languages here: bitcoin.org